April 08, 2024
How Traditional Recycling Could Be Putting You at Risk
Offices across the country share a similar problem: the amount of paper used is tremendous. Each year in the United Sates, offices use up to 12.1 trillion sheets of paper, which can have significant negative impacts on the environment. Paper alone accounts for approximately 26% of all landfill waste and 33% of municipal waste.
Recycling is the obvious solution for businesses and the planet. The World Counts estimates that each ton of recycled paper saves around 1,400 liters of oil, 26,500 liters of water, and 17 trees. However, companies may put themselves at risk by simply throwing documents with private information in the recycling bin.
With data security threats on the rise and the average U.S. breach costing $9.48 million, businesses can no longer consider data protection and security an optional investment. Protecting your confidential information begins by knowing exactly what happens to it during the disposal process.
Vulnerabilities of Traditional Document Disposal
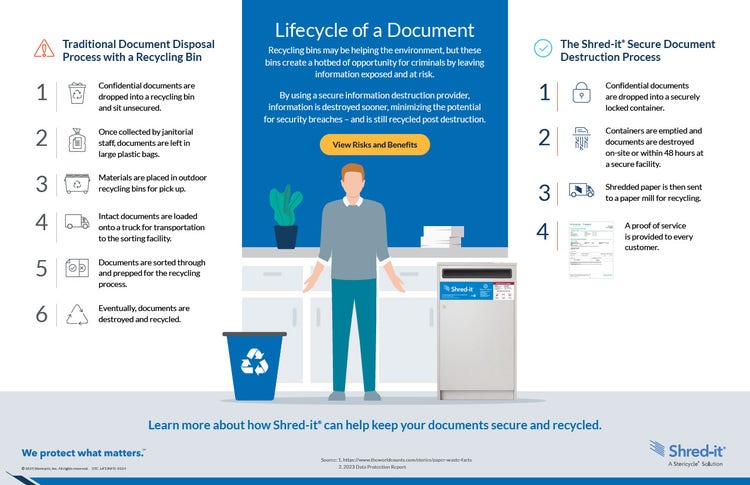
Did you know that nearly every point in the traditional paper recycling process puts you at risk of exposing confidential data? Here’s a breakdown of each step:
- Recycling Bins: Once employees finish using confidential documents, they drop them in the nearest blue recycling bin. This potentially exposes the contents to everyone in the office, including guests and others that normally wouldn’t have access to sensitive information.
- Collection Bags: Once collected, the documents are put in large plastic bags or bins, which may expose confidential information to anyone who passes by. According to the 2023 Shred-it ® Data Protection Report, 38% of all fraudsters come from within an organization.
- Outdoor Recycling Bins: Next , janitorial staff transfer disposed documents to outdoor recycling bins for pick up, giving people outside the building access to the confidential information. These outdoor bins are often not locked nor monitored, giving easy access to your data.
- Trucks: Recycling service professionals then load document waste onto a truck for transportation to a sorting facility. This provides an opportunity for downstream handlers, such as recycling workers, truck drivers, and others to access confidential information.
- Sorting Facility: Finally, the documents are delivered to the sorting facility where workers and volunteers sort and prepare them for recycling. These employees and volunteers could read, share, and steal sensitive information. Eventually, the recycling center recycles these documents, but businesses have no written documentation of when and where their secure documents were destroyed.
A Secure Solution: Disposal Done Right
Though high-profile cyber-attacks get the most media attention, physical data breaches still occur. Unless local regulations require the recycling of all paper with your local municipality, using a secure document shredding service, like Shred-it®, can keep data safe from the moment a document is thrown in a secure container or tote to the moment it is recycled. Paper documents disposed of with Shred-it® follow a seven-step destruction and recycling process:
- Employees drop their confidential documents in a secure Shred-it ® console. Unlike the traditional recycling disposal process, where any person in the office could view and take papers thrown away in blue bins, Shred-it ® consoles are locked and have a beveled slot to help prevent access to discarded documents.
- On a scheduled basis, Shred-it ® ’s team of professionals empties the consoles. The bins used in collecting and transporting secure information for destruction are molded from 100% recycled HDPE plastic.
- A Proof of Service Certificate is provided after every material pickup to acknowledge that your documents have been collected for secure destruction.
- The shredded and baled paper is then sold as sorted office paper, to be used in the manufacturing of paper products.
- A recycling facility subsequently turns the shredded paper into pulp by separating the paper’s fibers.
- The pulp is then put through a screening process that filters out impurities and prepares it for the removal of printing ink.
- Finally, the newly recycled pulp is mixed with fresh pulp to manufacture new paper products.
Safeguarding Your Business and the Planet
With corporate environmental responsibility top of mind for today’s businesses, secure paper disposal is about much more than business waste management. It’s also about protecting the environment and your relationship with customers, employees, partners, and the community.
With Shred-it®, you can feel confident that your information is safe every step of the way while doing your part to help reduce the environmental impact of paper waste. Globally in 2022, Stericycle securely shredded and recycled 1 billion pounds of paper.
Learn more about our secure document disposal process and the shredding service options to best meet your needs.